Overview
The School of Medicine Risk Management Project is a two-year plan to implement formal IT security risk management processes in collaboration with UCSF IT. The project will focus on:
IS-3 Implementation / Risk Management
IS-3, the UC-wide Information Security Policy, provides guidance on managing risk throughout decentralized units. Goals include:
- Document risk management and acceptance process
- Escalate risks to appropriate authorities for approvals
- Assign security leads for all departments
- Involve CAOs and chairs in risk decisions
Device Inventory
A comprehensive device inventory within our ServiceNow CMDB (Configuration Management Database) is essential for proper vulnerability management, incident response, and IT operations across UCSF. Devices include servers, workstations, network gear, storage devices, and printers. Assigning SOM device owners is key to ensuring smooth operations between departments and IT Security.
Patching and Vulnerability Management
Proper and timely patching of servers ensures that our systems are not vulnerable to exploits, keeping our data and applications adequately protected and available. Our goal is to have all departmentally managed servers establish a documented patch process, schedule, and cadence. Vulnerability scanning validates the patch process is working and provides detailed reporting prioritized by criticality to help prioritize your efforts. This service is provided in coordination with IT Security.
Application Inventory
Similar to device inventory, it’s important all SOM applications are inventoried in the CMDB so we know what applications are in use, what classification or data they have, who the application owners and administrators are, and where they are physically located. We aim to inventory all legacy P4 and P3 systems and integrate new-system documentation into the risk assessment process. Application owners will have access to edit and update their own applications to ensure records stay valid.
Risk Assessment
The UCSF security risk assessment is an administrative assessment that provides an accounting of required security controls as part of high-level review to gauge if compliance to policy and regulatory requirements is met. All P4 and P3 systems must go through the risk assessment process, which will help application owners ensure they meet all basic security controls before their systems are deployed. Our secondary goal is to create a streamlined process focused on user value.
Business Impact Analysis, Business Continuity Planning, Disaster Recovery (BIA, BCP, DR)
Business impact analysis (BIA), business continuity planning (BCP), and disaster recovery (DR) are three related but different processes that ensure operational resilience. Together they assess the criticality of business activities and make sure the people, processes, and technology are designed to protect against potential threats. The BIA has been integrated into the risk assessment process but additional planning is necessary for critical applications or systems that must be restored within 24 hours.
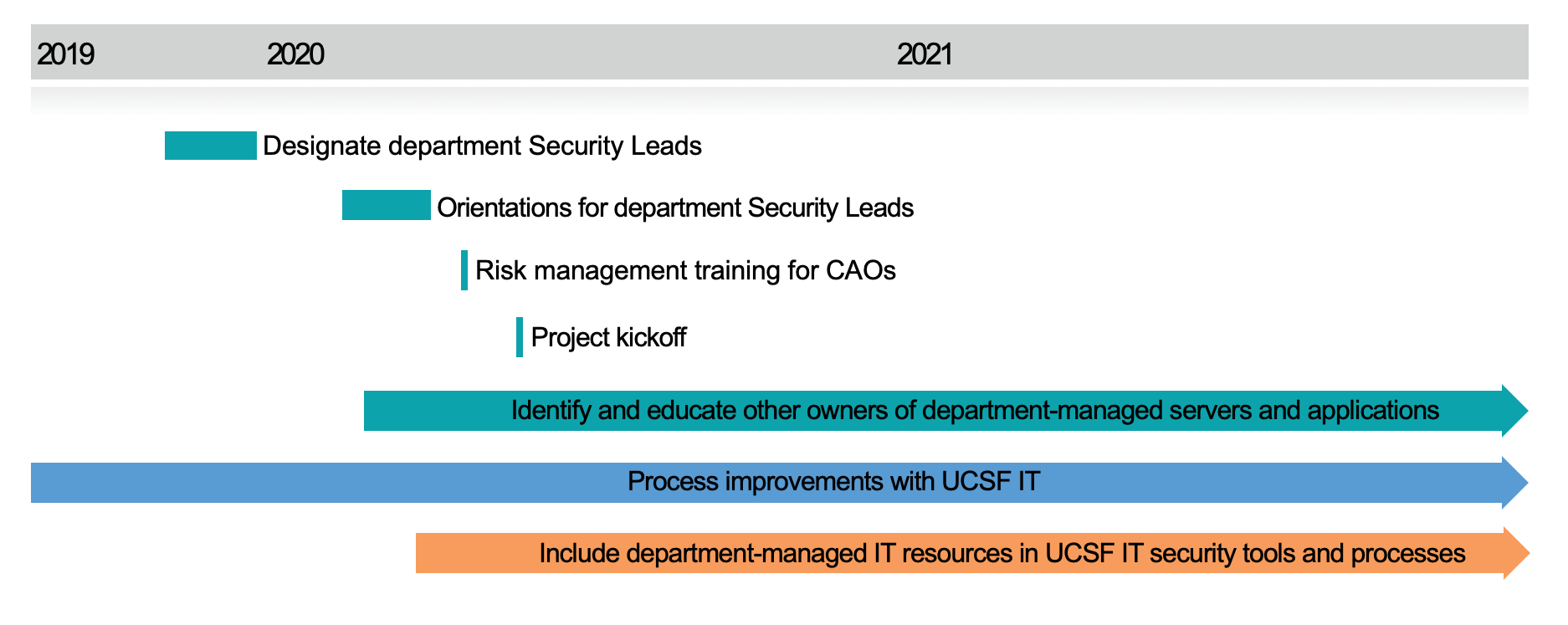
Timeline